- Ipsec For Mac Software
- Ipsec Machine Certificate
- Ipsec For Mac Catalina
- Ipsec For Mac Pro
- Sftp For Mac Osx
- Ipsec Mac Address
- Table of contents
- strongSwan on Mac OS X
- MacPorts, Building from the Git repository
Since strongSwan 4.3.4 the IKE daemon charon runs on macOS.
With 5.1.0 most limitations of earlier releases have been resolved. For instance, virtual IP addresses are now fully supported.
Please note that releases before 5.0.0 don't support IKEv1 because the old pluto IKEv1 daemon was not ported to macOS.
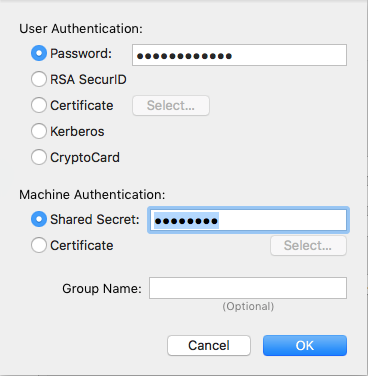
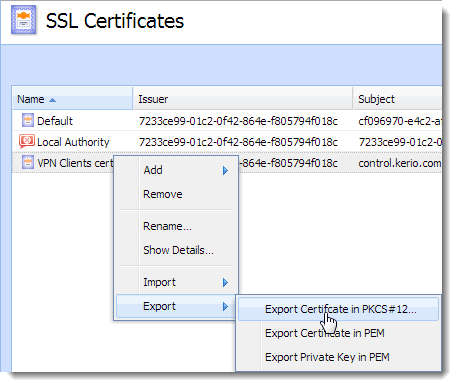
The Names Server and Client Certificates are used in order to distinguish between the Certificates used in the SonicWall (Server) and the Mac OS X L2TP/IPsec Client (Client). The Client Certificate used here has a Key Size of 1024 Bits.
Native application¶
We previously maintained a native application for Mac OS X 10.7 and newer. It allowed easy road-warrior access in a similar fashion as the NetworkManager integration does on Linux.
Ipsec For Mac Software
With the availability of the standard IKEv1/IKEv2 client integration in more recent versions of macOS, we have determined that continuing maintenance of a native application build is no longer required. For information on using the integrated VPN client in macOS, see Mac support.
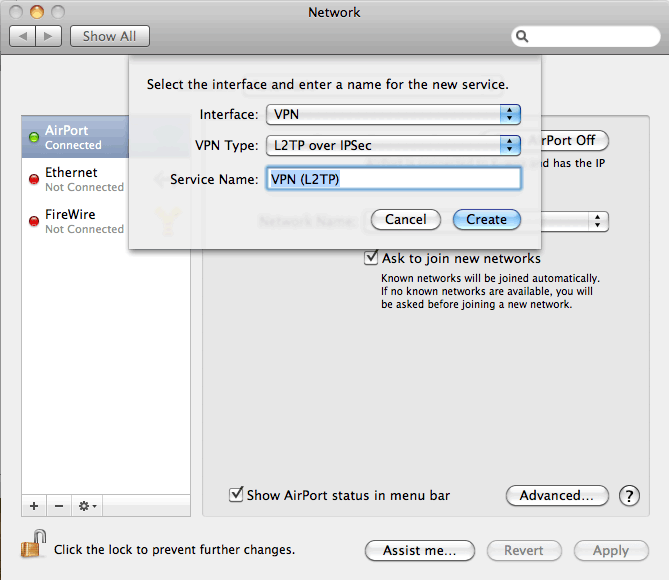
The client configuration described here is for a Mac OS X 10.8.2 (Mountain Lion). However, the configuration would be similar in other Mac OS X versions. The names server and client certificates are used in order to distinguish between the certificates used in the SonicWall (server) and the Mac OS X L2TP/IPsec client (client). This guide will show you how to connect to a VPN that supports the L2TP/IPSec protocol on your Apple MAC. Facebook: https://www.facebook.com/ricmedia.pchelp. As previously mentioned, Mac OS X now includes an IPsec stack in the form of KAME; it must be configured with a CLI. If you prefer a GUI to configure and launch your IPsec tunnels for Mac OS X, try Equinux, available for download as a 30-day trial.
It featured:
- An easy to deploy unprivileged strongSwan.app, providing a simple graphical user interface to manage and initiate connections
- Automatic installation of a privileged helper tool (IKE daemon)
- Gateway/CA certificates get fetched from the OS X Keychain service
- Currently supported are IKEv2 connections using EAP-MSCHAPv2 or EAP-MD5 client authentication
- The app does not send certificate requests. So unless the gateway's certificate is installed in the client's Keychain the server has to be configured with leftsendcert=always, otherwise, the client won't have the gateway's certificate available causing the authentication to fail.
- Requires a 64-bit Intel processor and OS X 10.7 or higher
Archived builds of strongSwan for OS X can be found on http://download.strongswan.org/osx.
Homebrew¶
As an alternative to the native app, strongSwan was recently added to Homebrew. The strongswan Formula makes installing and updating the current release very simple. The plugin configuration is most suitable for road-warrior access, that is, plugins specifically designed for use on gateways are disabled (e.g. attr or eap-radius).
sudo is not required to install strongSwan, but is later needed when running ipsec, swanctl, or charon-cmd.
MacPorts, Building from the Git repository¶
It's also possible to build strongSwan manually from the Git repository or a source tarball. When building from the Git repository it is recommended to use MacPorts to install the build dependencies. That's because some packages provided by Homebrew are unsuitable to build strongSwan from scratch.
Requirements¶
Ipsec Machine Certificate
If you build from the Git repository the tools/packages listed in source:HACKING have to be installed via MacPorts.
Depending on your plugin configuration other packages may be required, such as the GMP library or a newer release of the OpenSSL library.
Building strongSwan¶
The regular installation instructions may be followed to build strongSwan.
The following ./configure options are either required, or recommended:
--disable-kernel-netlink- Required to disable the Linux-specific kernel interface--enable-kernel-pfroute- Required to enable the interface to the Mac OS X network stack--enable-kernel-pfkey- Required to enable the interface to the Mac OS X IPsec stack. Alternatively, the--enable-kernel-libipsecoption may be used to enable strongSwan's userland IPsec implementation that provides support for AES-GCM (depending on plugin configuration) in IPsec processing, which the Mac OS X kernel currently does not--disable-gmp --enable-openssl- Recommended to avoid additional dependencies by using the system's OpenSSL library instead of the GMP library for public key cryptography--enable-osx-attr- Recommended to enable DNS server installation via SystemConfiguration--disable-scripts- Required because these scripts are not fully portable--with-lib-prefix=/opt/local- Required because MacPorts installs libraries and header files in/opt/local
Ipsec For Mac Catalina
Ipsec For Mac Pro
- For releases before 5.0.0 you also need to add
--disable-pluto.
Limitations¶
- Mac OS X 10.5 doesn't provide any means (e.g. IP_PKTINFO or IP_SENDSRCADDR) to set the source address of IPv4 UDP packets sent over wildcard sockets.
This could be a problem for multihomed gateways.
Due to the lack of policy based routes, virtual IPs can not be used (client-side).This has been resolved with 5.1.0 by using TUN devices.
Sftp For Mac Osx
The kernel-pfroute interface lacks some final tweaks to fully support MOBIKE.With 5.1.0 several improvements have been made in regards to network mobility. But due to a limitation of the Mac OS X kernel (IPsec SAs can't be updated if an IP address changes) IPsec SAs have to be rekeyed instead of updated with a simple MOBIKE message.
Ipsec Mac Address
